Internet of Vehicles (IoV) Solutions
Internet of Vehicles (IoV) Solutions
Background
/
BACKGROUND INTRODUCTION
>>>
Chinese government has successively promulgated laws and regulations to clarify the basic principles and systems requirements for data security, cross-border data flows management and cryptography applications, including:
- The Cybersecurity Law of the People's Republic of China
- Decision of the Standing Committee of the National People's Congress on Strengthening the Network Information Protection
- Cryptography Law of the People's Republic of China
Ministry of Industry and Information Technology of the People’s Republic of China (MIIT) and Standardization Administration of the People’s Republic of China (SAC) jointly released the:
- Guideline for Developing National Internet of Vehicles Industry Standard System (Intelligent & Connected Vehicle)
determine the standard system for intelligent connected vehicles, including general specification standards for information security.
The Key Task of Intelligent Connected Vehicles Standardization in 2018 proclaimed the vehicle cybersecurity standard to promote the data security standardization of the IoV in terms of data classification, evaluation of data protection capabilities and data encryption and desensitization and released standards:
- Technology Specification for Data Security of Internet of Vehicles Information Service
- Specification of Internet of Vehicles information Service – User Personal Information Protection
clarify the baseline requirements for IoV data security management and personal information protection.
At the same time, the State Cryptography Administration released:
- GM/T 0054-2018 General Requirements for Information System Cryptography Application
which raised systematic requirements for the cryptography construction and use of IoV information service.

REQUIREMENT ANALYSIS
/
REQUIREMENT ANALYSIS
>>>
The IoV cloud (TSP service) is located at the core of the entire system, connecting the suppliers and terminals (car and driver) to provide services. It faces challenges of the security requirements in cloud platform, key management, data security, access control, transmission networks and other cryptographic application scenarios.
The communication methods of the IoV are more diversified, and the sensitivity of data transmission is getting higher. It has to tackle the issue of the cryptographic applications requirements for private key protection, transmission protocols, identity legitimacy, and data confidentiality integrity on the network.
The IoV terminal adds more intelligent devices to the car terminal which caused vehicles facing a more complicated situation than before like smart ECU, more open network connection and OTA. Besides, firmware/software upgrades should resolve issue of authentication, reversible decompilation and data leakage modification, so more cryptographic application scenarios should be considered for IoV.
Application Case
/
APPLICATION CASE
>>>
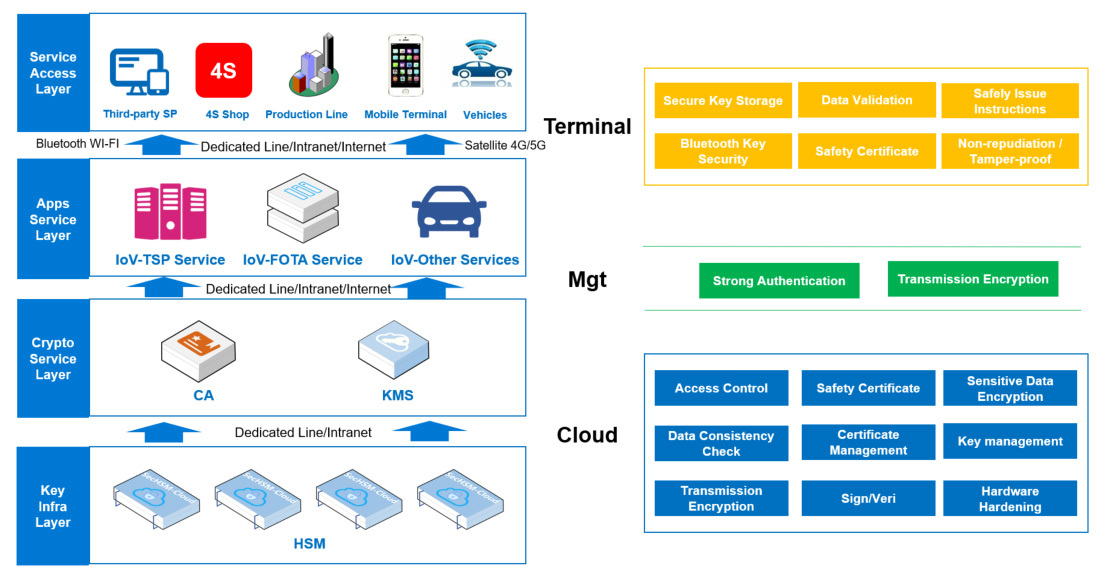
Cloud service (IoV service platform) deploys CA, KMS, Cloud HSM, DB HSM, delivery gateway and other security products and devices, to
- Enhance the cryptographic protection capabilities of key management, security authentication, transmission encryption, signature/verification, storage encryption and configuration log integrity for server-side business
- Control the terminals connected to the cloud from the first network connection
- Prevent illegal connections, strengthen access control and security authentication
- Solve the problem of identity validity authentication while the mobile and the vehicle terminal are connected to the cloud
- Verify data stored and received in the cloud
- Protect the secure storage of vehicle and owner information by integrated encrypted data
Protect the integrity of the configuration and operation log information.
Pipeline transmission (network communication), including the Internet connection between the terminal and cloud, and the NFC between the mobile and vehicle terminal. For Internet connections, our IoV solution can
- Combine the PKI Trust System and the TLS cryptographic protocol to establish a secure channel for data transmission between endpoints and cloud services
- Provide information transmission security
- Use digital signatures to verify the identity legality for NFC
- Ensure the mobile terminal connected to the vehicle is legal and reliable
Terminals include vehicle and mobile terminal, through mobile shields, white box, security interfaces and APP security protection:
- Provide identity and data validity verification
- Effectively solve problems of TSP security reinforcement, FOTA package legality detection
- Bluetooth keys secure delivery
- Communication information cleartext transmission
- Identity authentication of the connected parties
Case Sharing
/
CASE SHARING
>>>
AUTOAI
Daimler AG
Yutong Group
Foton Motor Group
Previous Page



