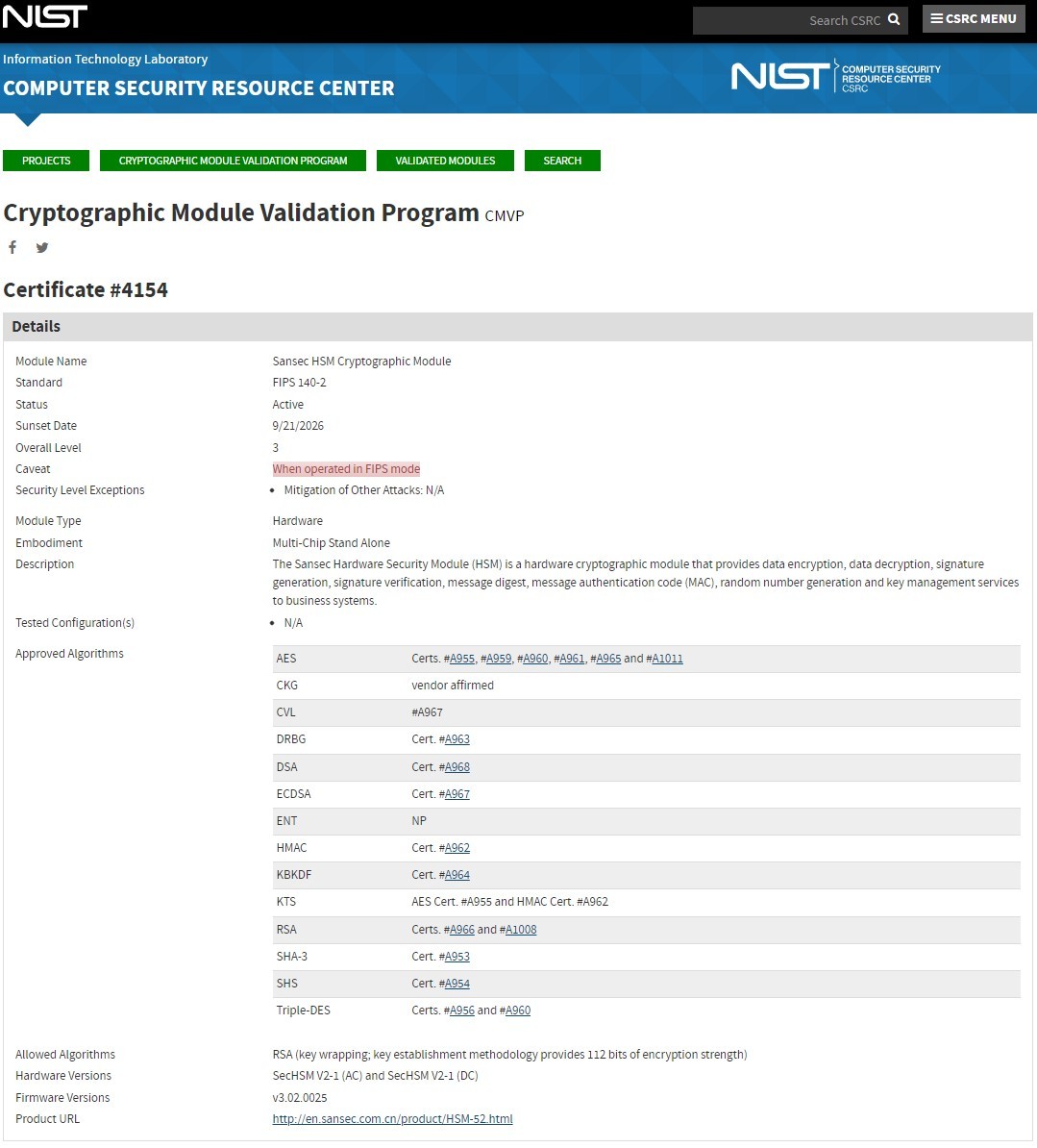
Sansec HSM Cryptographic Module
Sansec HSM Cryptographic Module
■ Product Introduction and Features
Sansec HSM Cryptographic Module is a fundamental cryptographic device independently developed by Sansec. It complies with FIPS 140-2 Level 3. It could be deployed into various kinds of cryptographic security systems to ensure the confidentiality, integrity, and effectiveness of the transmitted information through its digital signature and encryption. It has high-speed and multi-task parallel processing abilities. The product could be applied to financial, e-government, e-commerce, and enterprise information systems. This provides guarantee for the development of social informatization.

■ Application Features
Cryptographic Algorithm Support
Asymmetric algorithms: RSA, DSA, ECDSA, and EdDSA
Symmetric algorithms: DES/3DES
HASH algorithms: SHA1/SHA2/SHA3, and MD5
Key Management
Key generation, storage, backup, and restoration.
Random Number Generation
The generation of TRNG is based on physical noise sources, which meets FIPS140-2 requirements.
User Access Control
Hierarchical management of access users to improve the security of HSM.
Support Standard Interface
The API interface supports international interface standards such as PKCS#11, MS-CSP, JCE, etc.
Supports a rich set of application instructions.
Multi-parallel
Improve the performance of cryptographic operations
Fault tolerance, which does not impact on the business continuity when one HSM fails.
Personal PIN Assurance
PIN BLOCK encryption, conversion, verification, etc.
Personal Validity verification
PVV calculation and verification
Card Validity Verification
CVV calculation and verification
Financial Parameter Verification
ARQC generation, ARPC verification, etc.
Convert Encryption
Supports PIN, key, or data convert encryption.
■ Product Advantages

System security
HSM realizes the authorization and authentication to the application server through the support of crypto connection and whitelist, which further improve the security of the system.

Key Security
Adopt the multi-layer key structure to thoroughly guarantee the security of keys and application systems.

Compliance
FIPS140-2 Level 3
Previous Page
Next Page
Previous Page
Next Page